- 31Jul2018
-
Google Chrome 68 makes HTTPS mandatory - Is Your Website Ready?
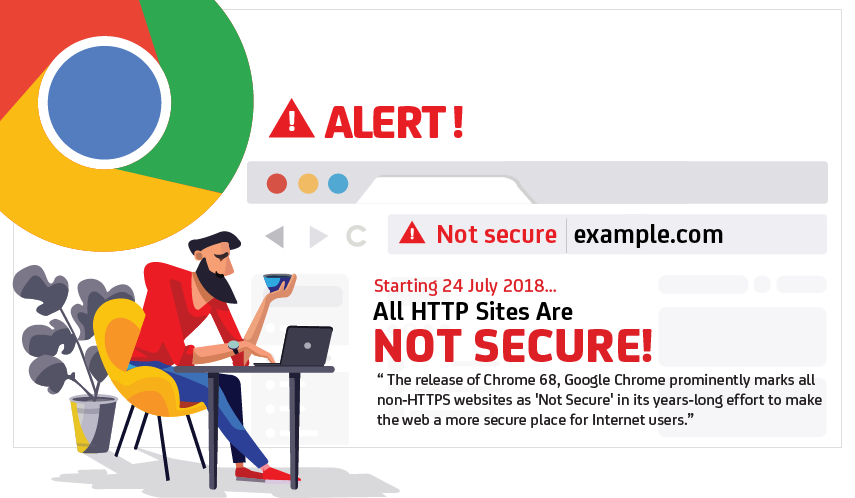
Starting 24th July 2018, when Google Chrome 68 is released, every website that is not running HTTPS will be labelled as “not secure” in the address bar.
- Last update: 31 July 2018